1. Encryption of Data at Rest and in Transit
Encrypted Phones: These devices are designed with additional layers of security, including encryption of data both at rest (stored on the device) and in transit (during transmission). This means that even if the device falls into the wrong hands, the information remains inaccessible without the corresponding encryption key. Nowadays, the evolution of encrypted cell phones has made them reliable devices available to everyone.
Conventional Telephones: Although many conventional phones offer some level of encryption, it is typically not as robust as phones specifically designed with a focus on security. Basic encryption may be optional or absent on some mainstream models.
2. Secure Operating System
Encrypted Phones: They often use highly secure operating systems and MDMs that create a secure environment within the system to customize them in a way that limits the risk of vulnerabilities. Additionally, these phones often receive faster and more regular security updates. What is an MDM and how do they make your cell phone more secure?
Conventional Telephones: Many conventional phones use more common operating systems, which can be more susceptible to attacks and threats. Security updates may take longer to arrive due to the variety of devices and manufacturers.
3. Protection against Malware and Threats
Encrypted Phones: They are designed to better resist malware attacks and other threats. Pre-installed applications and controlled environments reduce malware risks.
Conventional Telephones: They may be more vulnerable to the installation of malicious apps, especially if they are downloaded from untrustworthy sources. The diversity of operating systems and models can also make them more attractive targets for certain attacks.
Would you like to learn how to know if your cell phone is hacked?
4. Privacy of Calls and Messages
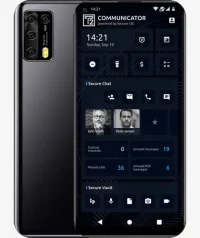
Encrypted Phones: Encrypted phones offer features such as end-to-end encrypted calls and messages with military security, ensuring that only the sender and receiver can access the content.
Conventional Telephones: Although many conventional applications offer encryption, it is quite basic and not all of them guarantee complete privacy of communications. Some may store metadata or be susceptible to unauthorized access. Additionally, the same companies that provide telephone and internet service are the first to collect information. Do you know what information your operator collects from you?
5. Features and Applications
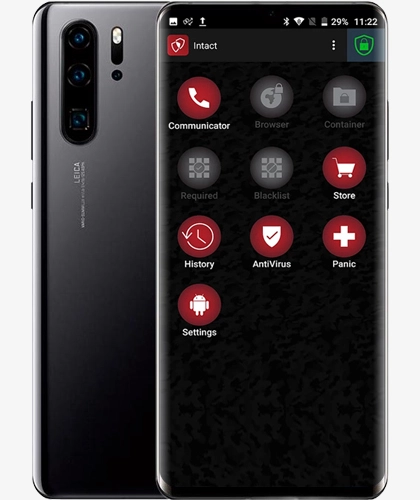
Encrypted Phones: Encrypted phones come with their own secure application store that limits access and security breaches, and also have features such as remote deletion, self-destructing messages, blocking screenshots, wallets for Cryptocurrencies and an IMSI catcher detector.
Conventional Phones: By having access to any type of application, even from links, they are quite prone to cyberattacks, and functionalities that encrypted phones have already had for many years are just beginning to be implemented.
Clearly, today, it is becoming more and more common for people to lean towards cybersecurity and privacy, and year after year we will see how this trend continues to grow among consumers. However, if you still plan to wait a while to purchase an encrypted phone, we recommend the best methods to guarantee the security of your smartphone.