

Communication data is protected by 521-bit ECC, double ratcheting and extended triple diffie-Hellman

Ghost does not create international loopholes in its cryptosystems to bypass encryption. no back doors

Enhanced protection of stored data with strong security measures against malicious online and offline brute force attacks
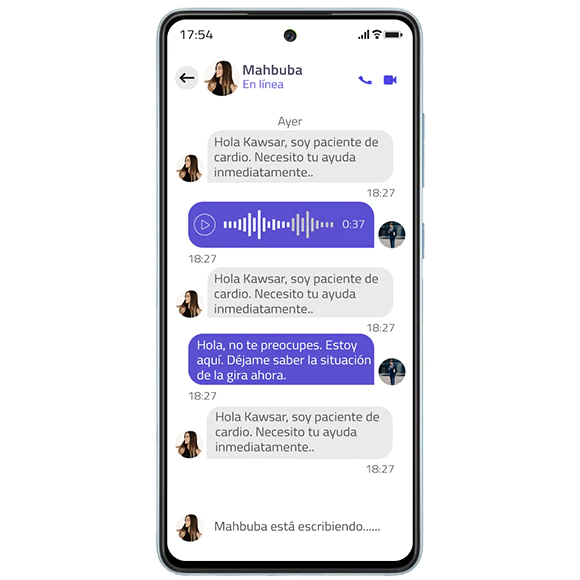
All messages sent and received from the device are encrypted to ensure private communications.
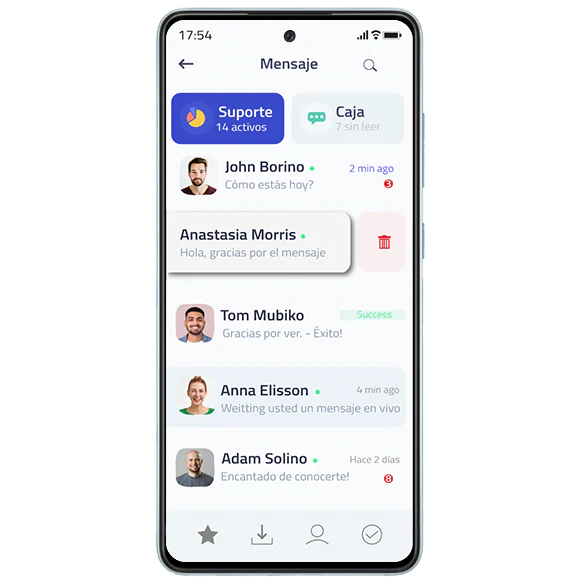
Ghost uses hybrid encryption with complex mathematical data processing with end-to-end encryption without any chat data being stored on any server
No malicious third party can access the information. With Ghost's military encryption you can be sure that your communications will be protected at the highest level of security.

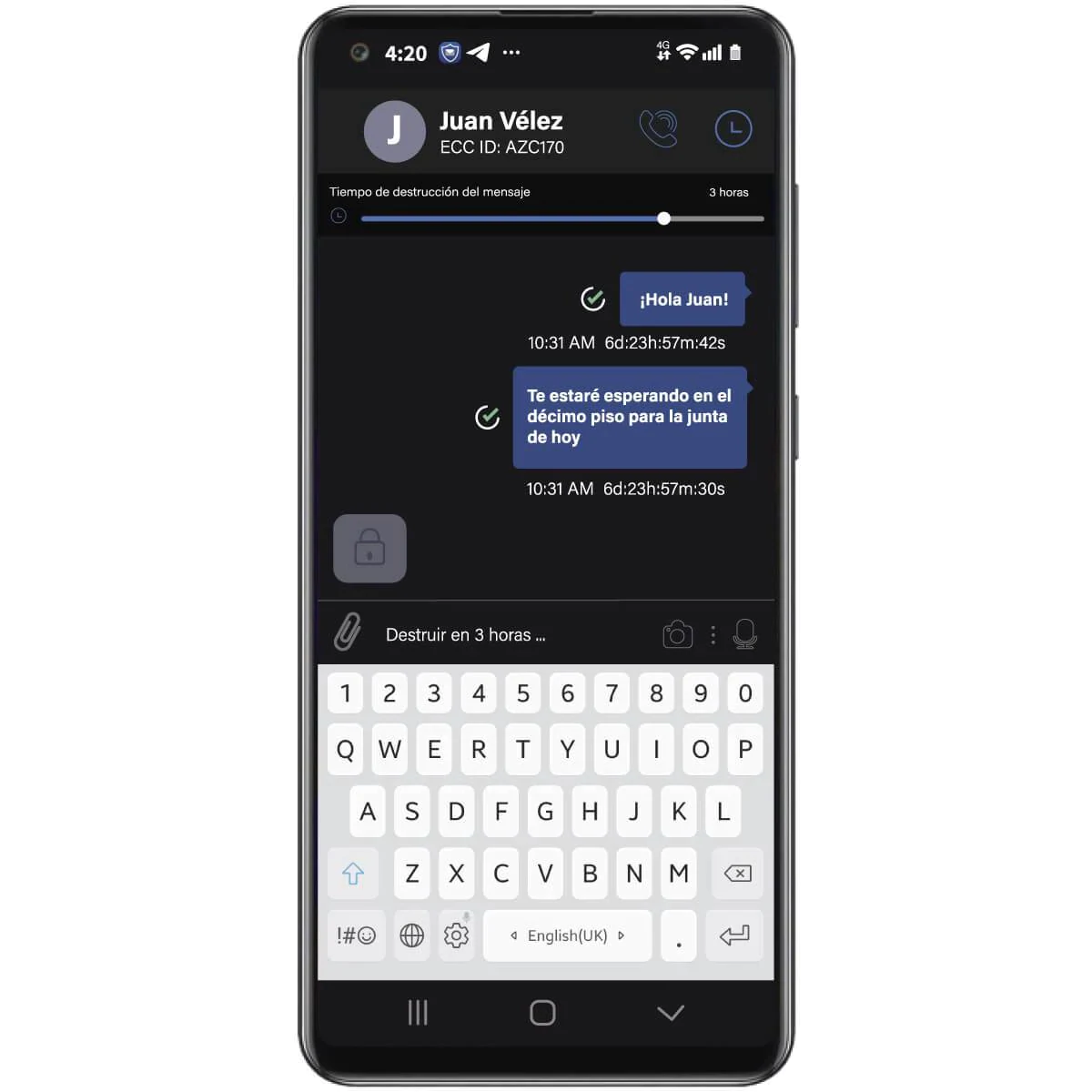
Create group chats with a timer. When this expires, the group chat will automatically self-destruct on all members' devices without leaving any traces.

Create group chats with full features in anonymous name privacy to protect the identity of the participants.

Communication is encrypted and protected from user to user and is transmitted through our decentralized network. All data stored on devices is protected and encrypted

Real-time voice encryption
Secure and private end-to-end encrypted voice calls that cannot be eavesdropped on by us or third parties.


Ghost uses hybrid encryption with complex mathematical data processing with end-to-end encryption without any chat data being stored on any server
No malicious third party can access the information. With Ghost's military encryption you can be sure that your communications will be protected at the highest level of security.

With Ghost you can create a panic password that when entered, immediately deletes all information and messages from the device.

If your device is lost or stolen, you can perform a remote wipe to remove all data regardless of whether or not it's connected to the internet.

Ghost allows you to install apps from third parties to make communications more versatile

Protect yourself from cybercriminals and
keep safe your personal information!

Data or minutes


Data or minutes

Protect yourself from cybercriminals and
keep safe your personal information!
The panic password feature allows you to set a code to use in case of duress. This will silently erase all the data inside the phone.
In addition to the security and privacy offered by an encrypted cell phone, there will be features such as encrypted chats, remote deletion, encrypted mail, timed messages, cloud storage and multiple encrypted applications.
A remote wipe of the phone can be performed by contacting the provider, this in case the cell phone has been stolen, lost or seized.


BTC, ETH, USDT, DOGE, DAI, Etc...
T
BTC, ETH, USDT, DOGE, DAI, Etc...
Using the wrong network (blockchain) will result in the loss of funds.
Total a pagar:
N°
Send to @encriptados on Telegram your order number and your payment receipt to confirm your order.
Total:
N°
Bancolombia
Cuenta Ahorros: 259 804315 01
Nit: S901054325-9
Nombre de empresa: Safesolf Internacional SAS
Para inscribir la cuenta en Bancolombia debe quitar el -9 del nit
Send to @encriptados on Telegram your order number and your payment receipt to confirm your order.
Go to Encriptados' TelegramSteps:
1. Go to the nearest Crypto ATM
2. Select "Buy Bitcoin"
3. Enter the value of your purchase
4. Scan the barcode (that we present to you)
5. Enter the value of your purchase in cash
6. Confirm your purchase
7. Take a photo of the completed transaction.
Send to @encriptados on Telegram your order number and your proof of payment, to confirm your order.
Only deposit the value of your purchase, we assume the cost of the ATM transaction
Click here and get your code for ATM payment
Total:
N°

Send to @encriptados on Telegram your order number and your payment receipt to confirm your order.
