

Reverse entry of your PIN notifies emergency contacts of the situation and erases messages and content from the app vault.

For encrypted storage of images, videos, notes, and voice files.

Mask your app's UI to look like WhatsApp or other popular apps
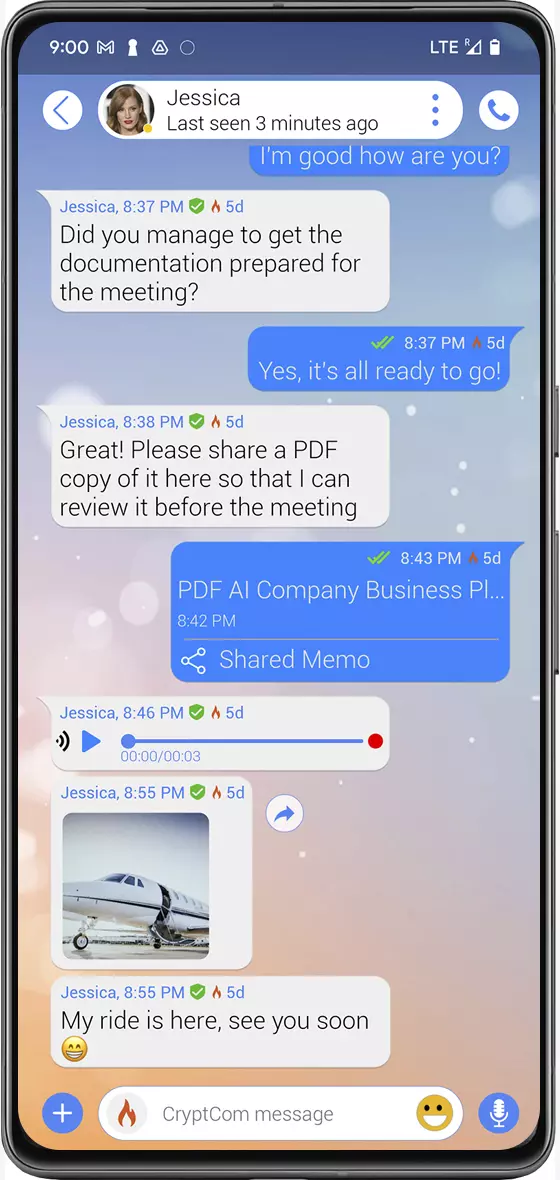
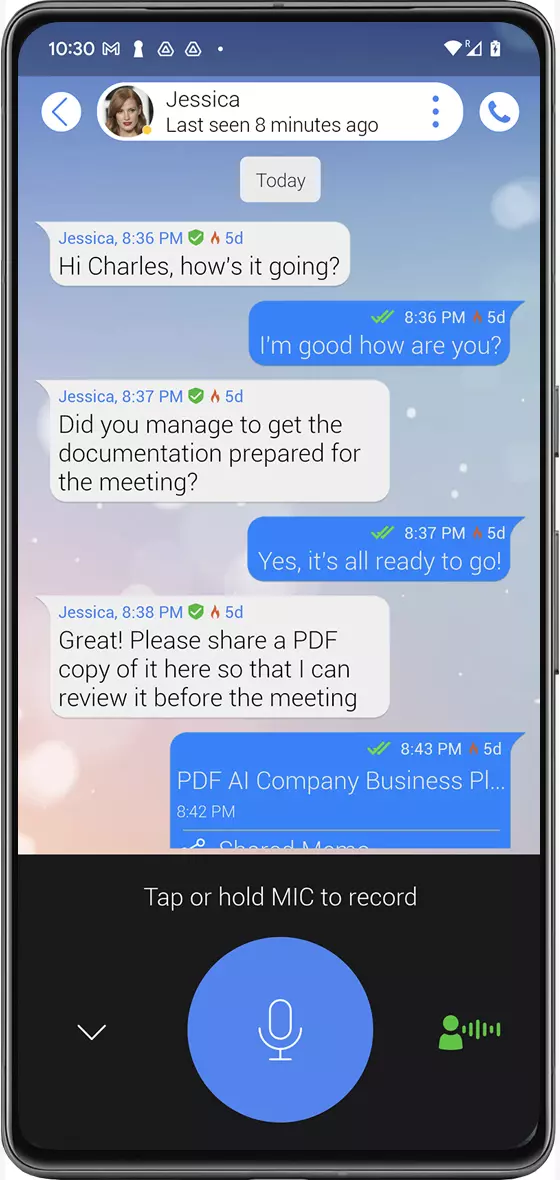
Encrypted Chats
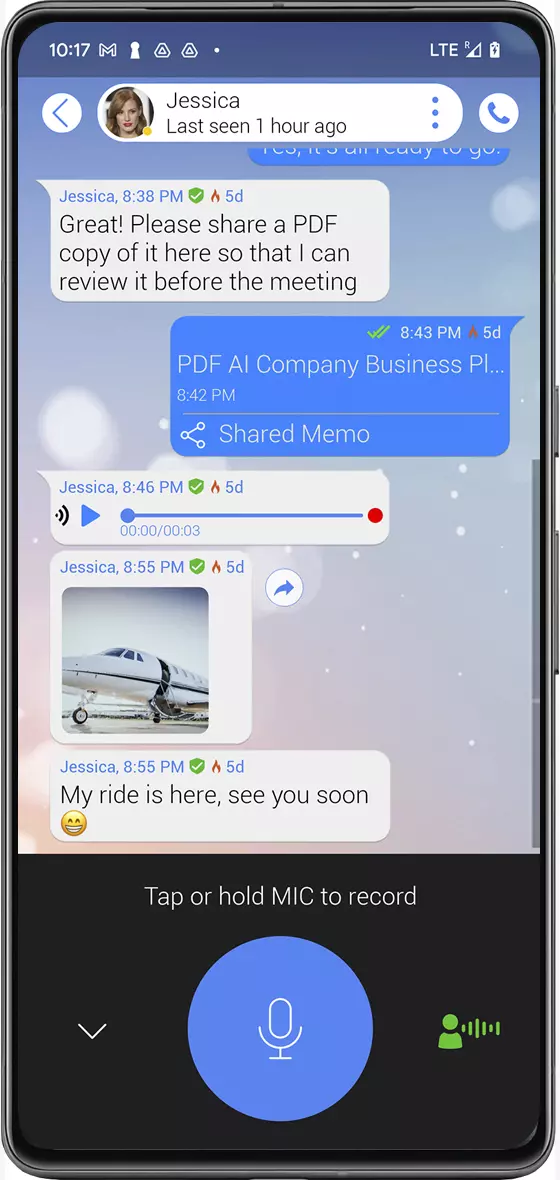
Send text, images, voice notes and videos securely and encrypted.
Group chat
With the option of anonymous groups of
zero knowledge, users will not be able to see or
retrieve contact information for
group members.
Combined chat messaging
and encrypted email
Hybrid encrypted chats in live chat view with notification delivered and read checkmarks, message editing and deleting features, text translation, and
recording timer for self-destruction of messages from users' devices.
Text masking
The text becomes a font
masked unreadable when the device is idle.

To stay connected with other contacts, within the safe hidden space on the device, you can add Signal, Threema, Silent Circle and others secure apps.

Private encryption keys are generated and securely stored only on mobile devices. unique keys of session and by message.

Use the PIN sequence to quickly and securely delete all app content and messages.
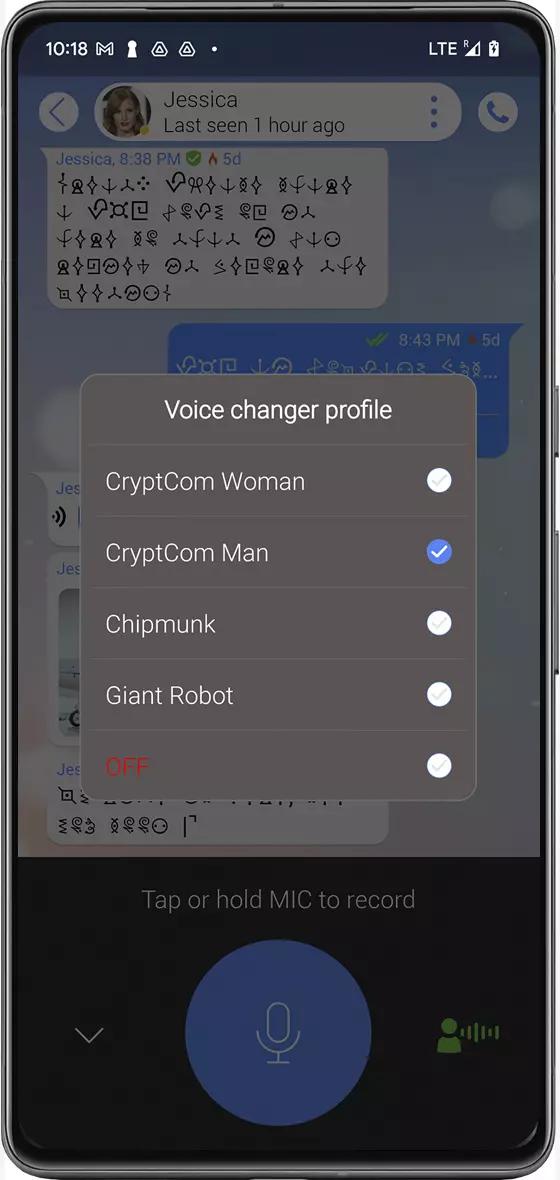
Voice calls and messages
voice encrypted
With algorithm voice changer
sure
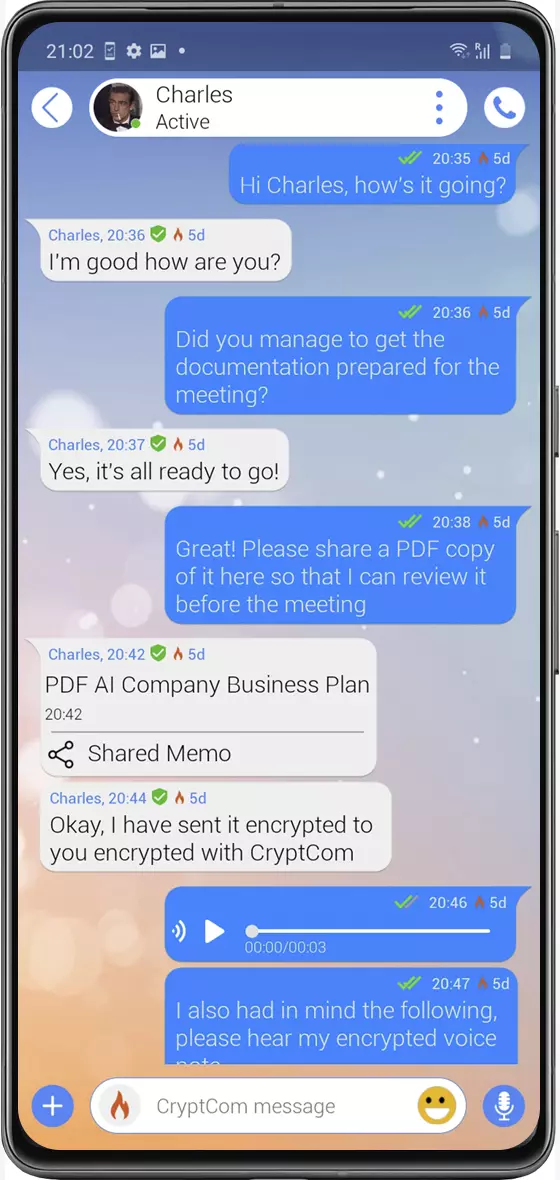
Encrypted email
Hybrid encrypted emails with delivered and read notification checkmarks, message editing and deletion features, text translation, and recording timer for self-destructing messages from users' devices.
Grab Proof
El dispositivo se desconecta automáticamente si se arrebata de las manos de los usuarios o si el dispositivo se sacude fuertemente.

For added security, automatic updates are not possible

Servers are destroyed every 24 hours after transfer to one without a trace.


The device looks like a normal Android phone.

Equivalente a más de 15 360 bits RSA

Apps will be locked and hidden if the device is shaken or picked up.


Apps will be locked and hidden if the device is shaken or picked up.

Tampering and inactivity criteria set by the user will cause the device to be wiped.

Use the PIN sequence to quickly and securely delete all app content and messages.

Protect yourself from cybercriminals and
keep safe your personal information!

for your purchase


for your purchase

Protect yourself from cybercriminals and
keep safe your personal information!
By encrypting the cell phone with a Cryptcom license, the original operating system is replaced by a military-grade encrypted one, with special features such as encrypted chats, secure calls, remote destruction, among others that you can learn about at encriptados.io
In addition to the security and privacy offered by the Cryptcom encrypted cell phone, there will be features such as encrypted chats, remote deletion, encrypted mail, timed messages, cloud storage and multiple encrypted applications.
In case of losing the phone or being a victim of theft, a predetermined combination of characters can be sent to the chat of your Cryptcom cell phone, to eliminate all the information. In other cases, it can be done by contacting the license provider.



Copyright © 2023 Safesolf International sas Inc. All rights reserved.
| Total: |
| N° |
Click here and get your code for payment
Bancolombia
Cuenta Ahorros: 259 804315 01
Nit: 901054325-9
Nombre de empresa: Safesolf Internacional SAS
Para inscribir la cuenta en bancolombia debe quitar el -9 del nit
Send to @encriptados on Telegram your order number and your payment receipt to confirm your order.
| Total: |
| N° |
Click here and get your code for payment
Tether Trx Address
TM7o86VCpQaS17NBe1zVdCuxv8J6qUm7eS

Send to @encriptados on Telegram your order number and your payment receipt to confirm your order.
| Total: |
| N° |
Steps:
1. Go to the nearest Crypto ATM
2. Select "Buy Bitcoin"
3. Enter the value of your purchase
4. Scan the barcode (that we present to you)
5. Enter the value of your purchase in cash
6. Confirm your purchase
7. Take a photo of the completed transaction.
Send to @encryptados on Telegram your order number and your proof of payment, to confirm your order.
Only deposit the value of your purchase, we assume the cost of the ATM transaction
Click here and get your code for ATM payment
Bitcoin address![]()
bc1qarlp0dugaxusdzknwqaydssss6vh6y5mxkjaes

Send to @encriptados on Telegram your order number and your payment receipt to confirm your order.
| Plan | |
| License | |
| Plan | |
| Value to buy | |
| Unit value | |
| Amount |
|
|
|
40$ USD |
| Coupon | |
| Discount |
0$ USD |
| Shipping |
40 USD
|
| Total |
0
|
|
|
|
|
|
|
