

In today’s digital landscape, where protecting personal information is essential, creating strong and secure passwords is essential to safeguard sensitive accounts and data. Here are the best practices for designing and maintaining strong passwords, ensuring your online privacy and strengthening your defenses against potential cyber threats.
Length and complexity are key elements of a strong password. Opt for passwords that contain at least 12 characters, combining letters (Upper and lower case), numbers and special characters. Avoid using easily accessible or predictable personal information, such as names and dates of birth.
Avoid using common passwords and predictable patterns, such as “123456” or “password.” Cybercriminals often conduct brute force attacks using known combinations, so it is crucial to create a unique password for each account.
The practice of regularly updating passwords is essential to maintaining security. Set reminders to change your passwords periodically, especially on sensitive or critical accounts. This measure reduces the likelihood that a compromised password will remain effective for a long period.
Two-factor authentication adds an extra layer of security. Enable 2FA whenever possible, as it requires identity verification through a second method, such as a code sent to your phone or an authenticator app.
Avoid storing passwords in unsafe places, such as notes on your desktop or in your web browser.
Stay informed on the latest security threats and techniques. Continued awareness and education are essential to adapt to changing security practices and understand emerging threats.
Use online tools to check if your passwords have been compromised in known security breaches. If you find any vulnerability, change your password immediately.
Protect your devices physically and control access to your passwords. Avoid leaving devices unlocked and don’t share passwords recklessly.
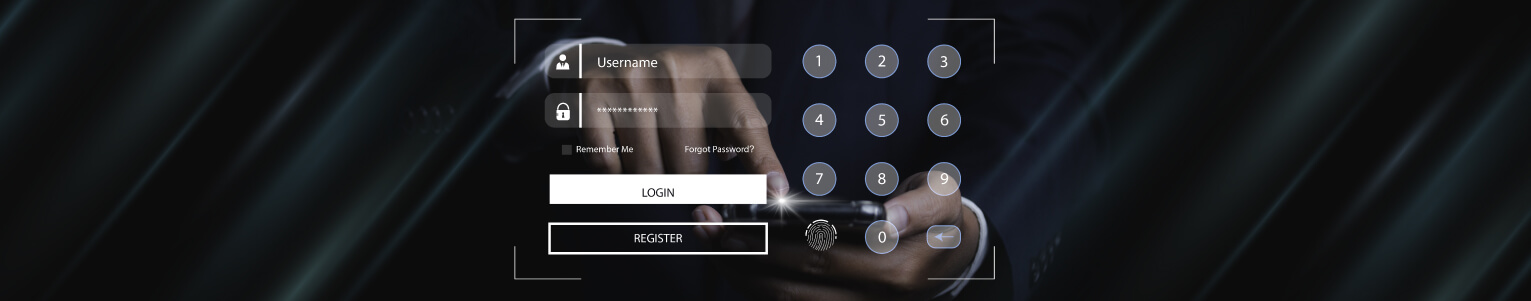
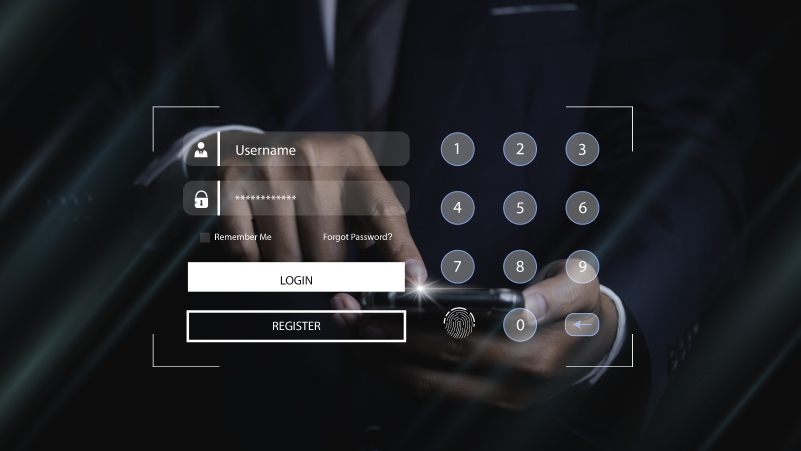
At Encriptados we are experts in digital security, we have the best encrypted applications to communicate safely with totally private messaging, you can also find the encrypted SIM Card that works in more than 200 countries offering security and anonymity. In addition, we have the best brands of encrypted cell phones that will turn your cell phone into an ultra-secure and impenetrable device.


BTC, ETH, USDT, DOGE, DAI, Etc...
T
BTC, ETH, USDT, DOGE, DAI, Etc...
Using the wrong network (blockchain) will result in the loss of funds.
Total a pagar:
N°
Send to @encriptados on Telegram your order number and your payment receipt to confirm your order.
Total:
N°
Bancolombia
Cuenta Ahorros: 259 804315 01
Nit: S901054325-9
Nombre de empresa: Safesolf Internacional SAS
Para inscribir la cuenta en Bancolombia debe quitar el -9 del nit
Send to @encriptados on Telegram your order number and your payment receipt to confirm your order.
Go to Encriptados' TelegramSteps:
1. Go to the nearest Crypto ATM
2. Select "Buy Bitcoin"
3. Enter the value of your purchase
4. Scan the barcode (that we present to you)
5. Enter the value of your purchase in cash
6. Confirm your purchase
7. Take a photo of the completed transaction.
Send to @encriptados on Telegram your order number and your proof of payment, to confirm your order.
Only deposit the value of your purchase, we assume the cost of the ATM transaction
Click here and get your code for ATM payment
Total:
N°

Send to @encriptados on Telegram your order number and your payment receipt to confirm your order.
