
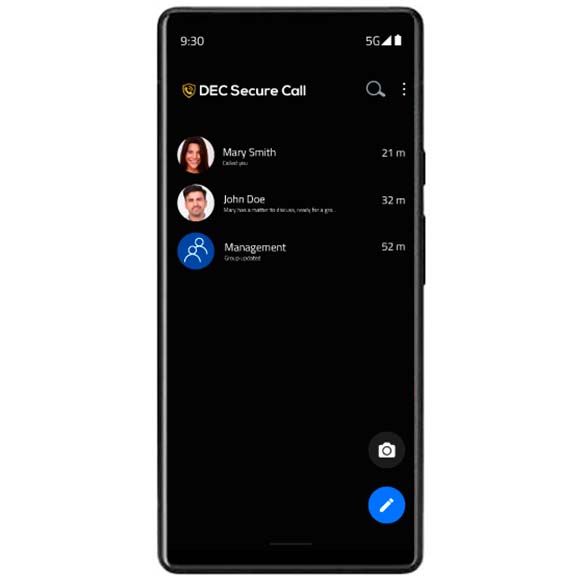
List of independent contacts
The dedicated Secure Call contact list is inaccessible from outside the app, keeping your Secure Call contacts private and discreet.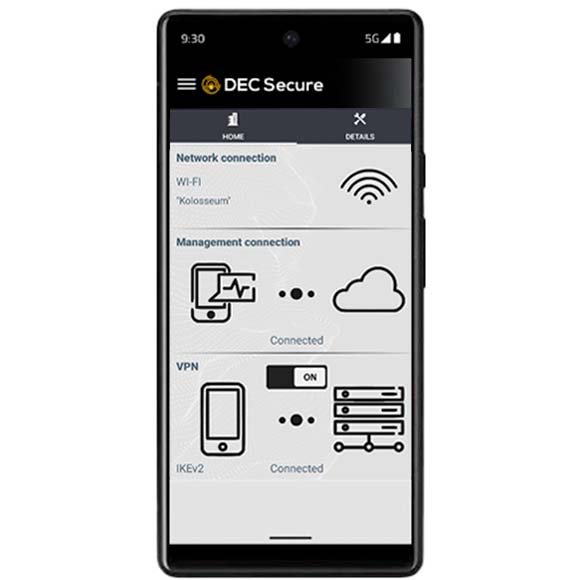

List of independent contacts
The dedicated Secure Call contact list is inaccessible from outside the app, keeping your Secure Call contacts private and discreet.

List of independent contacts
The dedicated Secure Call contact list is inaccessible from outside the app, keeping your Secure Call contacts private and discreet.
Encrypted mobile devices designed, assembled and tested to ensure their integrity. Optimum operation with the operating system, rigorous manufacturing procedures, security, reinforced tests and quality assurance.

Operating system with unbreakable cybersecurity technology, security patches, updated against emerging threats and intuitive user interface. Full disk encryption.

We continually develop additional layers of security, making information theft virtually impossible. This guarantees our users a private communication and beyond the reach of any espionage attempt.
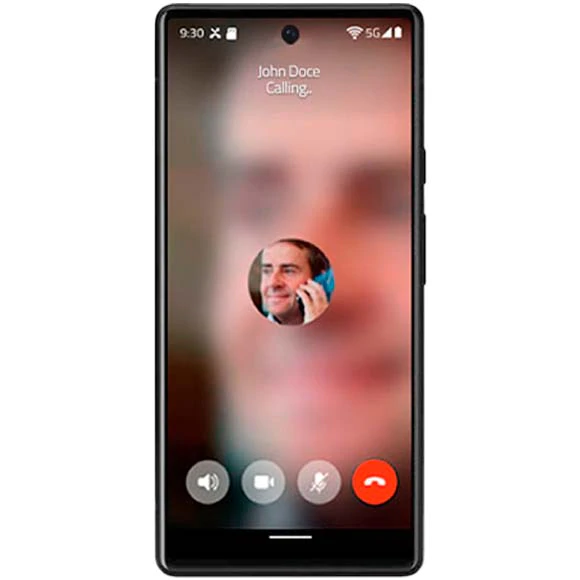

DEC Secure Call gives you everything you'd expect in a secure communications app, including always-on AES-256 encryption; individual and group voice calls, video calls and messaging Your communications are 100% private, we cannot listen to your calls or read your messages under any circumstances, and nothing is stored on our servers.



DEC Secure Call gives you everything you'd expect in a secure communications app, including always-on AES-256 encryption; individual and group voice calls, video calls and messaging Your communications are 100% private, we cannot listen to your calls or read your messages under any circumstances, and nothing is stored on our servers.


We keep you connected securely and privately
We not only protect your data on the smartphone, but also make sure that your web browsing, transactions and communications are also protected.

Automatically connects with automated authentication, not allowing you to send or receive unprotected data

A sophisticated network security and threat detection and response program thwarts the efforts of cyber attackers

It prevents all unauthenticated and unencrypted connections, eliminating the possibility of inappropriate exposure.
Mobile App Management
Managed private app library to deliver apps to the device without a connection to public clouds.
Apps
whitelist Complete whitelist of apps to stop downloading, or deploying spyware or inappropriate apps.
Approved apps only
Our team has independently reviewed each app in the library to validate security and privacy criteria.

Send and receive images, audio, video, and other files online with messaging to share your most private information securely and efficiently.

Automatic message deletion and screenshot prevention prevent the risk of inappropriate content sharing.

No communication history information is stored on DEC's servers and there is no way to access or intercept messages.


Multi-container functionality known as "Safe Zones" allows the use of a single device to manage personal and private data separately and securely.

Access workspaces from the home screen and switch between safe zones by swiping left or right.

Each safe zone has its own security policies for data isolation, including separate PIN code protections.

Remote management of your mobile device
DEC Secure provides remote and centralized management of your generic Android security features

Administrative management of over 100 different individualized device policy settings to mitigate attack vectors you didn't know existed.

Remotely lock your device or send a command that instantly wipes all data, eliminating the risk of exposure due to loss or theft.

Automatically obtain and install firmware updates, keeping the device updated and complying with security policies.

Protect yourself from cybercriminals and
keep safe your personal information!

Data or minutes


Data or minutes

Protect yourself from cybercriminals and
keep safe your personal information!
By encrypting the cell phone, the original operating system is replaced by a military-grade encrypted one, with special features such as encrypted chats, secure calls, remote destruction, among others that you can learn about at encriptados.io
In addition to the security and privacy offered by an encrypted cell phone, there will be features such as encrypted chats, remote deletion, encrypted mail, timed messages, cloud storage and multiple encrypted applications.
In case of losing the phone or being a victim of theft, a predetermined combination of characters can be sent to the chat itself to eliminate all the information on the cell phone. In other cases, it can be done by contacting the license provider.


BTC, ETH, USDT, DOGE, DAI, Etc...
T
BTC, ETH, USDT, DOGE, DAI, Etc...
Using the wrong network (blockchain) will result in the loss of funds.
Total a pagar:
N°
Send to @encriptados on Telegram your order number and your payment receipt to confirm your order.
Total:
N°
Bancolombia
Cuenta Ahorros: 259 804315 01
Nit: S901054325-9
Nombre de empresa: Safesolf Internacional SAS
Para inscribir la cuenta en Bancolombia debe quitar el -9 del nit
Send to @encriptados on Telegram your order number and your payment receipt to confirm your order.
Go to Encriptados' TelegramSteps:
1. Go to the nearest Crypto ATM
2. Select "Buy Bitcoin"
3. Enter the value of your purchase
4. Scan the barcode (that we present to you)
5. Enter the value of your purchase in cash
6. Confirm your purchase
7. Take a photo of the completed transaction.
Send to @encriptados on Telegram your order number and your proof of payment, to confirm your order.
Only deposit the value of your purchase, we assume the cost of the ATM transaction
Click here and get your code for ATM payment
Total:
N°

Send to @encriptados on Telegram your order number and your payment receipt to confirm your order.
