

Encrypted mobile devices designed, assembled and tested to ensure their integrity. Optimum operation with the operating system, rigorous manufacturing procedures, security, reinforced tests and quality assurance.

Operating system with unbreakable cybersecurity technology, security patches, updated against emerging threats and intuitive user interface. Full disk encryption.

We continually develop additional layers of security, making information theft virtually impossible. This guarantees our users a private communication and beyond the reach of any espionage attempt.
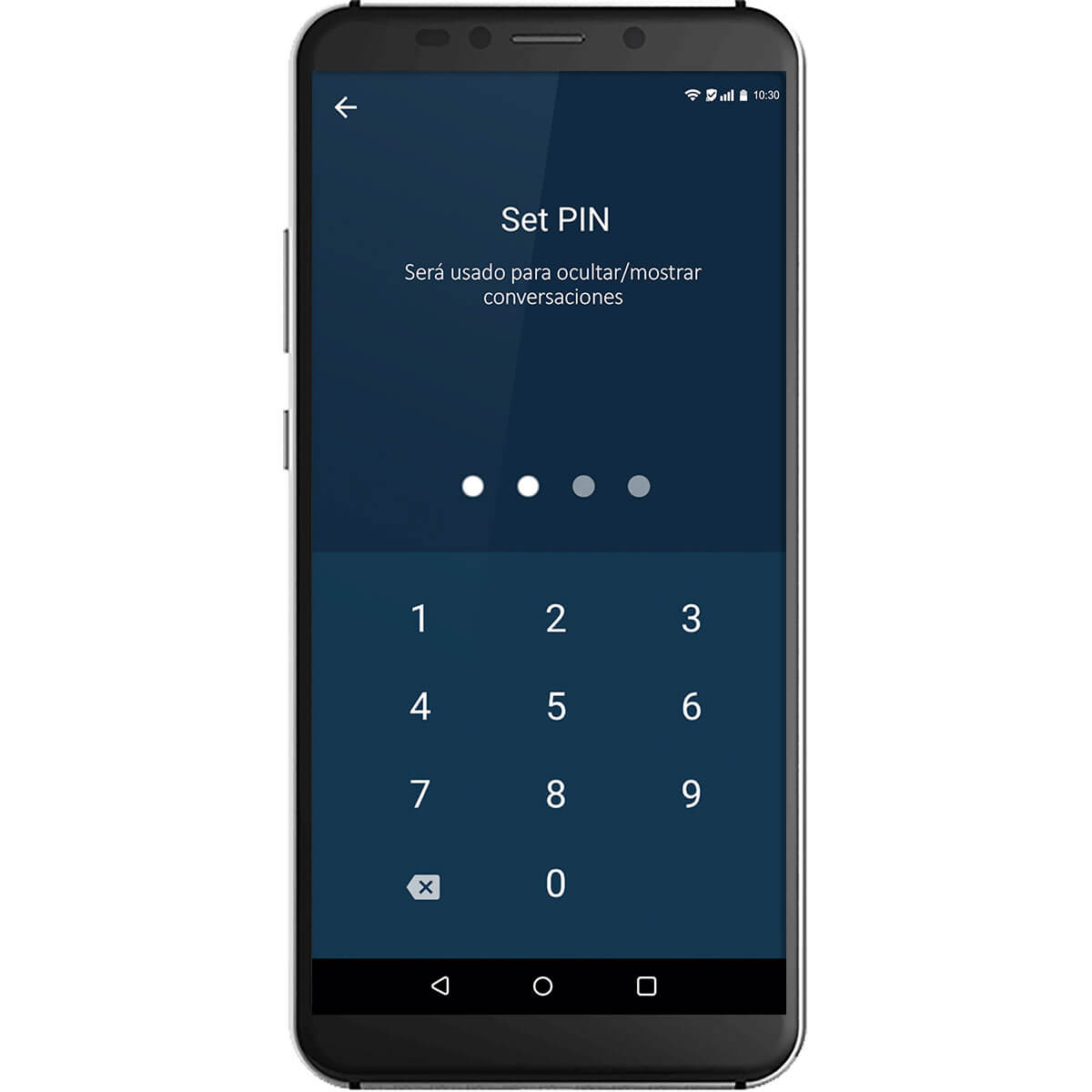
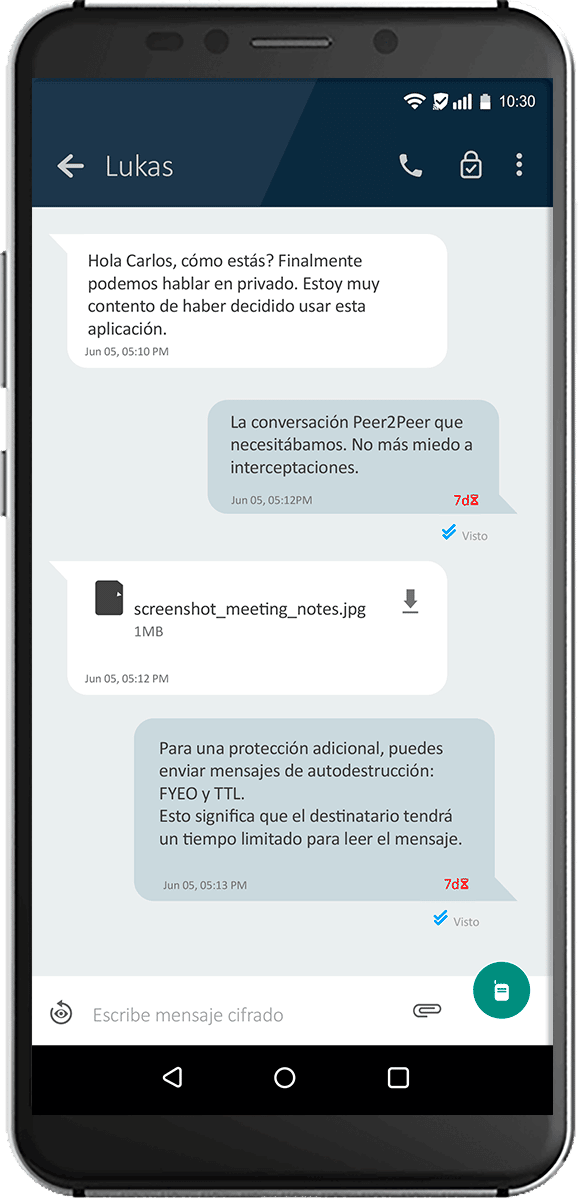
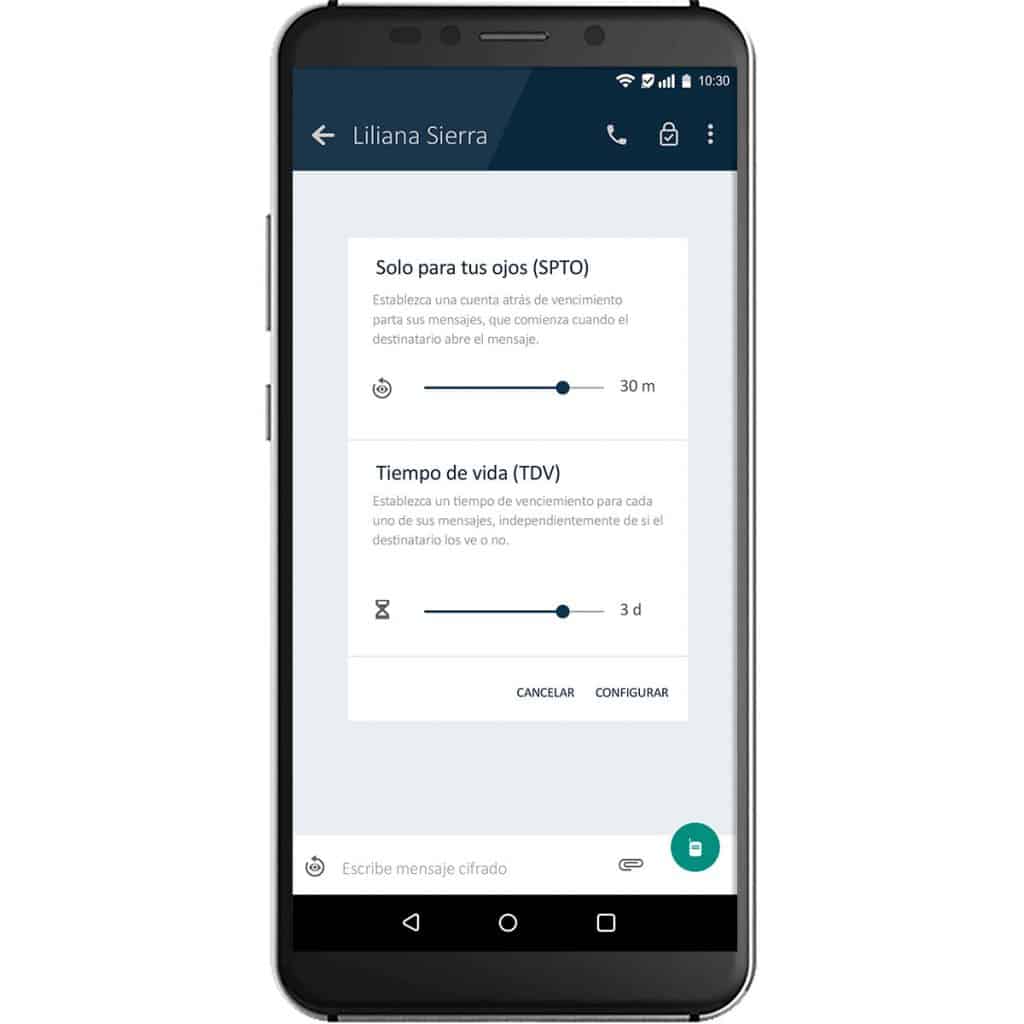



Ensures that our users' communication is private and out of reach.

Switch to desktop with BlockChain Applications or Work Encrypted Applications by activating work mode.

To ensure that our users' communication is private and out of reach.
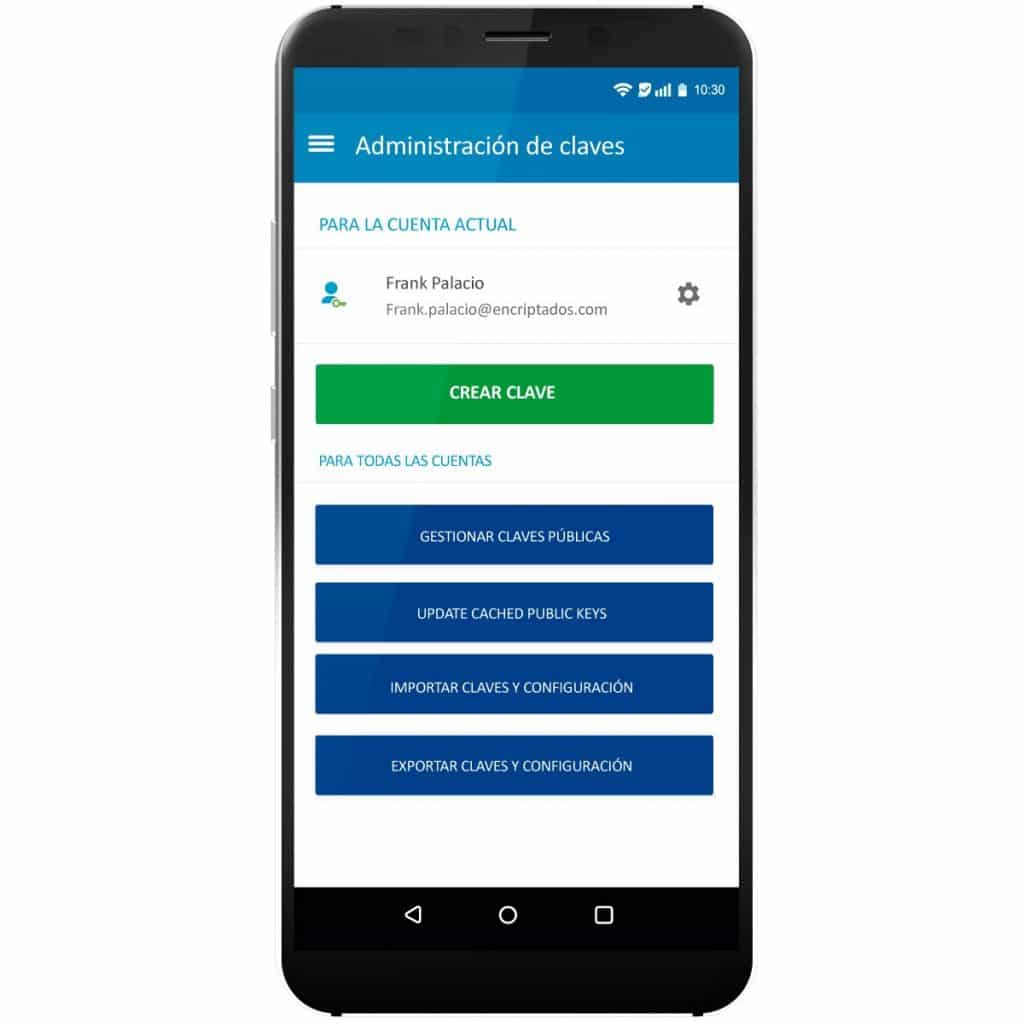
Email Military grade encryption: We use PGP protocol, with 4096-bit keys and AES-256 encryption. So no one can decrypt your emails.
PGP encrypted key control:
Keys are generated and stored only on the device. This way, only you will be able to access the copies of them.
Encrypted application database:
All your emails, contact names, registrations and the encryption keys you use for your messages are stored in the application, inside an encrypted database.
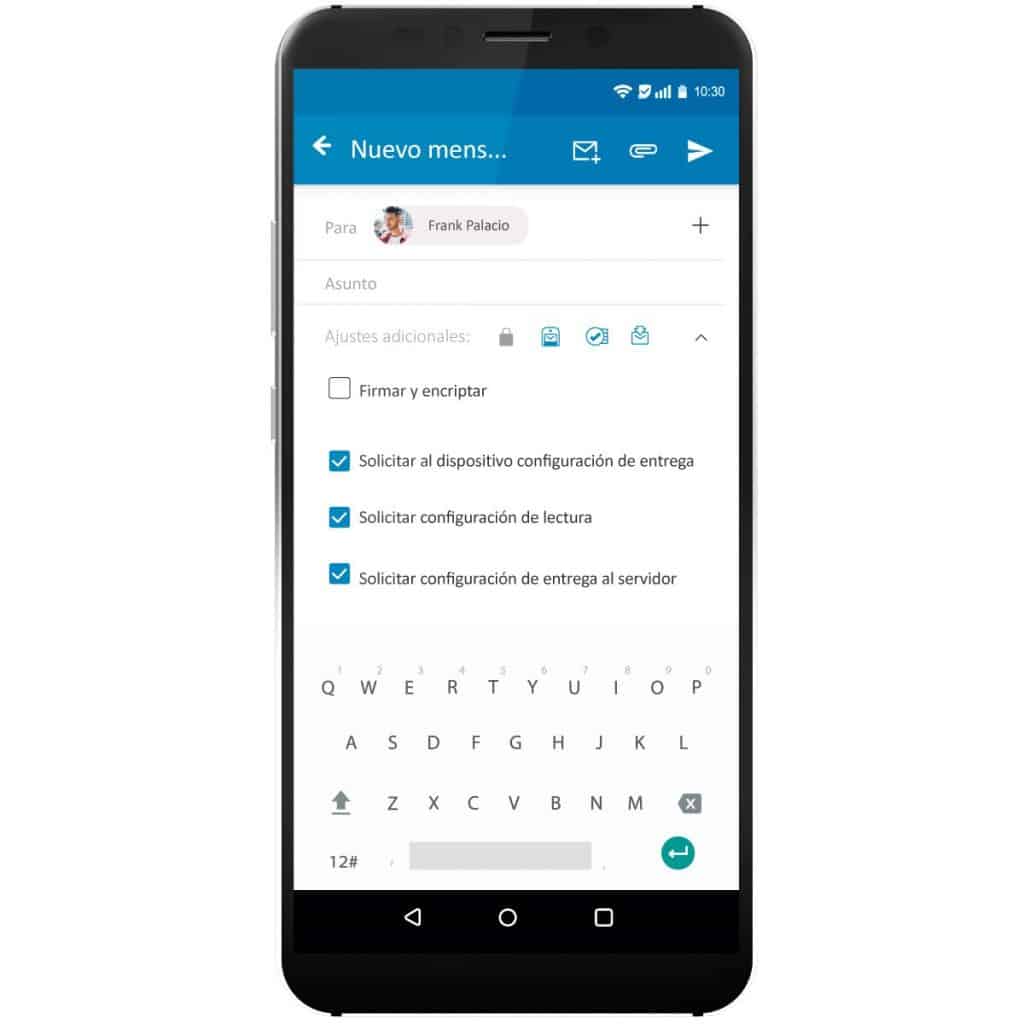
Open communication network: The service does not include blacklisted or whitelisted domains. We have an open network that allows you to communicate with everyone.
Send unencrypted emails:
Secure email communication is not restricted to just PGP clients. You can also send regular unencrypted emails to anyone.
Encrypted Drafts:
Sometimes you don't want to send a message right away. If you save it to secure email, the draft will be encrypted.
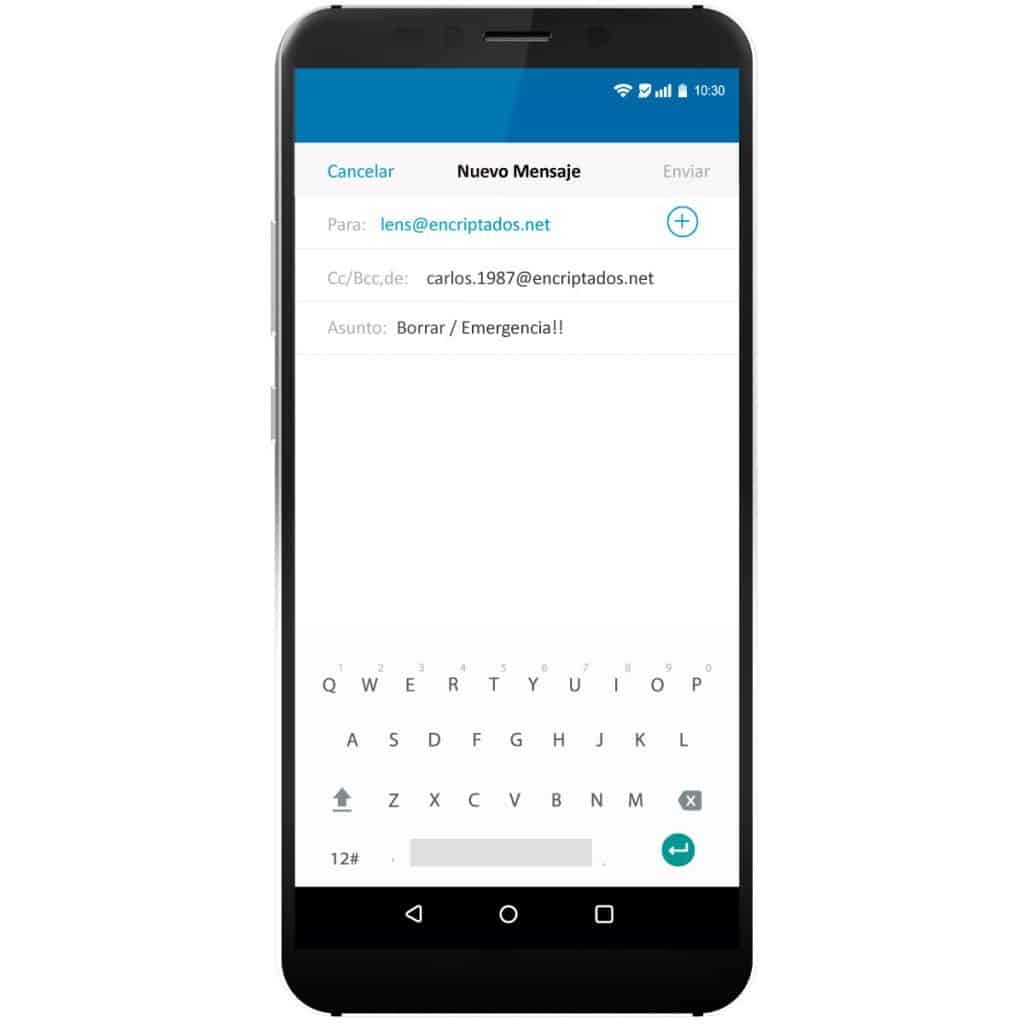
Remote wipe option by email: Are you worried that someone will take your phone and extract data from it? You can use secure email to erase everything on the phone.
Multiple accounts:
Like any contemporary email client, the application can support multiple accounts. Switching from one to another is easy, you can do it from the application.
High compatibility:
compatible with competing products that use the same version of the PGP protocol.
Security Lock Inbox rules:
If you receive a lot of emails, sorting them could be a problem. Secure Email allows you to create folders and rules (filters) to easily organize your inbox.
Export backups:
You can create a backup of your settings and encryption keys, to export them for use on another device.

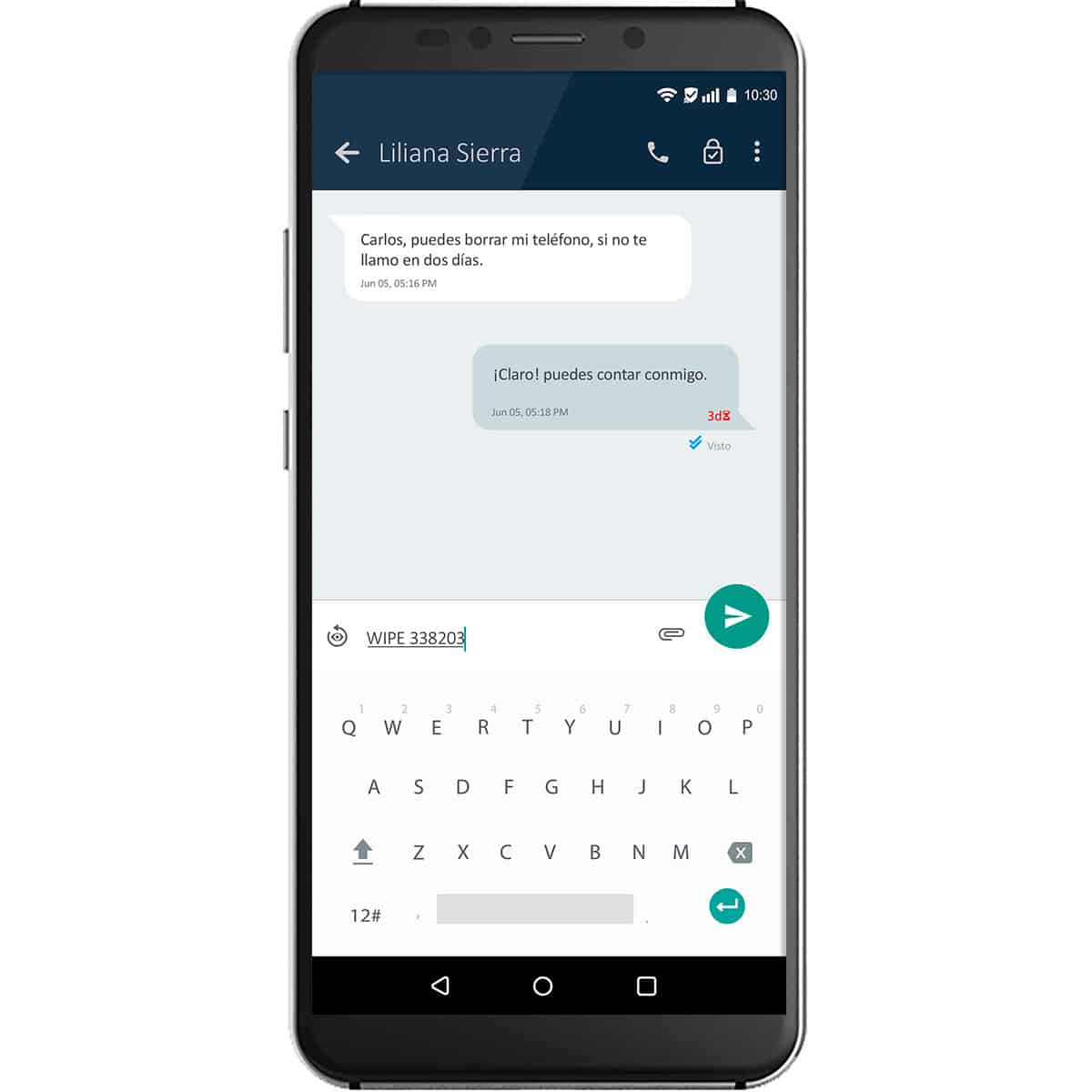
Even if you lose your phone, the information you have stored is absolutely safe, because you can remotely delete any data by sending a pre-determined combination of characters as a message to your secure chat.

To ensure that our users' communication is private and out of reach of any eavesdropping attempts, we continuously develop system updates.

Normal Android/iOS operating system with commonly used applications, activating incognito mode.
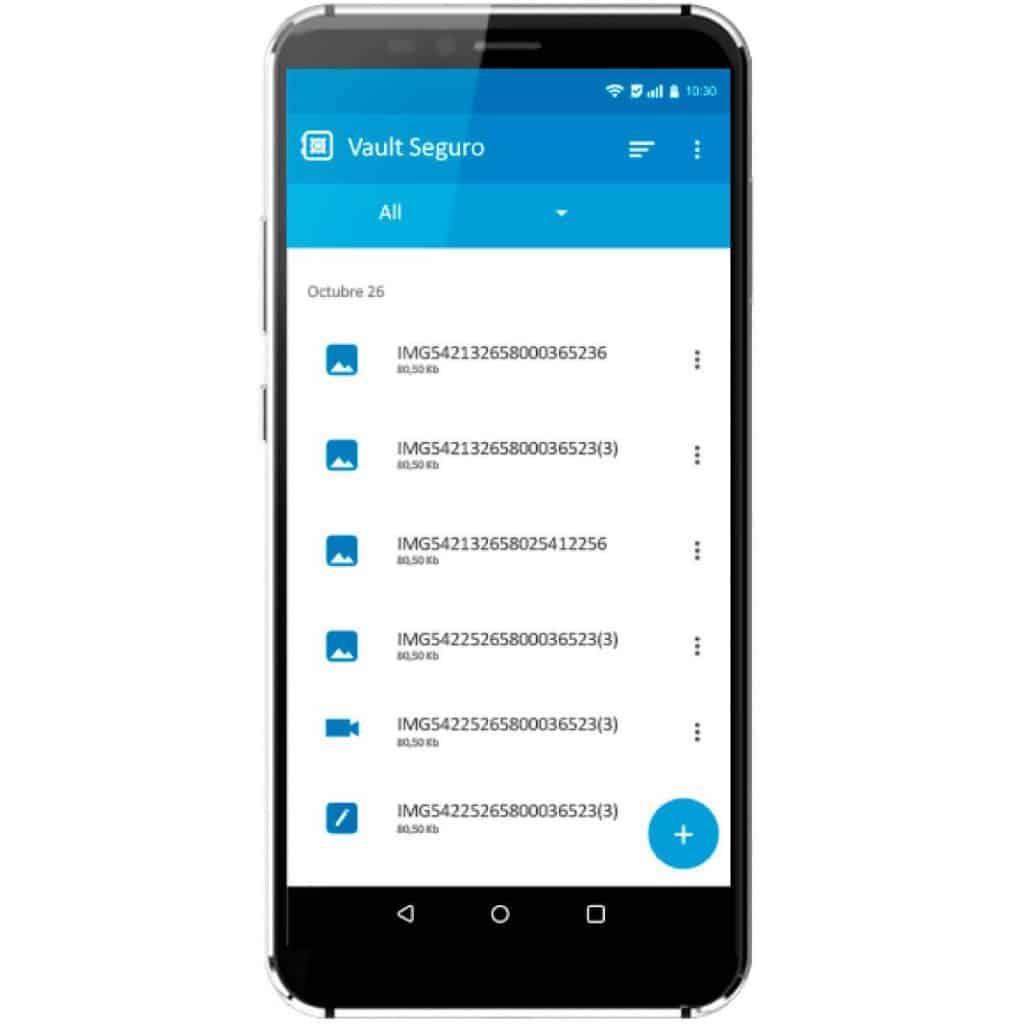
Allows you to store any message or file you want in the encrypted file container in the cloud.
Supported attachments.

OS Emergency Center with quick access to features you may need in urgent situations.
Quick Clean: Erase all data on the device with a single swipe.
Incognito mode: Transform the operating system into a normal Android and hide all your encrypted communication.

Protect yourself from cybercriminals and
keep safe your personal information!

for your purchase


for your purchase

Protect yourself from cybercriminals and
keep safe your personal information!
By encrypting the cell phone, the original operating system is replaced by a military-grade encrypted one, with special features such as encrypted chats, secure calls, remote destruction, among others that you can learn about at encriptados.io
In addition to the security and privacy offered by an encrypted cell phone, there will be features such as encrypted chats, remote deletion, encrypted mail, timed messages, cloud storage and multiple encrypted applications.
In case of losing the phone or being a victim of theft, a predetermined combination of characters can be sent to the chat itself to eliminate all the information on the cell phone. In other cases, it can be done by contacting the license provider.



Copyright © 2023 Safesolf International sas Inc. All rights reserved.
| Total: |
| N° |
Click here and get your code for payment
Bancolombia
Cuenta Ahorros: 259 804315 01
Nit: 901054325-9
Nombre de empresa: Safesolf Internacional SAS
Para inscribir la cuenta en bancolombia debe quitar el -9 del nit
Send to @encriptados on Telegram your order number and your payment receipt to confirm your order.
| Total: |
| N° |
Click here and get your code for payment
Tether Trx Address
TM7o86VCpQaS17NBe1zVdCuxv8J6qUm7eS

Send to @encriptados on Telegram your order number and your payment receipt to confirm your order.
| Total: |
| N° |
Steps:
1. Go to the nearest Crypto ATM
2. Select "Buy Bitcoin"
3. Enter the value of your purchase
4. Scan the barcode (that we present to you)
5. Enter the value of your purchase in cash
6. Confirm your purchase
7. Take a photo of the completed transaction.
Send to @encryptados on Telegram your order number and your proof of payment, to confirm your order.
Only deposit the value of your purchase, we assume the cost of the ATM transaction
Click here and get your code for ATM payment
Bitcoin address![]()
bc1qarlp0dugaxusdzknwqaydssss6vh6y5mxkjaes

Send to @encriptados on Telegram your order number and your payment receipt to confirm your order.
| Plan | |
| License | |
| Plan | |
| Value to buy | |
| Unit value | |
| Amount |
|
|
|
40$ USD |
| Coupon | |
| Discount |
0$ USD |
| Shipping |
40 USD
|
| Total |
0
|
|
|
|
|
|
|
